Free Website Assessment and Network Consultation available now for Small Businesses!
- Business Benefits
- Attacks
- How to Secure the Business
- Solutions You Need
- Get Started
Benefits of Secure Network
Among the many benefits of securing business networks, the most importance ones include: to engender customer Trust; decrease the costs of data theft, loss of business resources; to enhance productivity by offering increased mobility with in-built safety (like unshackled Wi-Fi access with security); protecting the businesses against loss or reputation (reputation attacks, for example); allow for seamless business functioning and business continuity and finally, to ensure that the business meets legal norms, compliance requirements (Sarbanes Oxley Act) , etc, that bind down the network security clauses into business workings.
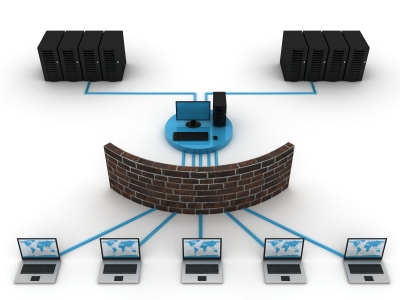
Network Security Threats: What Are We Worried About?
Digital vermin plagues the Internet today and it will be the first point of contact for all business networks to be attacked from -- viruses, Trojans, malware, Spyware, Phishing (and its various forms) attempts, DOS
(Denial of Service) attacks and DDOS (Distributed Denial of Service attacks; reputation attacks, Clickjacking and more. As if this wasn’t enough you have employee generated problems -- all the way corporate data embezzlement to harmless chatting over unsecured networks -- which are insider initiated and are even more difficult to combat with. Often, businesses also have to deal with zero-day attacks (the latest viruses) which are indeed lethal and you wouldn’t even know unless you are attacked.
- Secure the network infrastructure: Protocols like NAC (Network Access Control) are slated to mark this new demand. To secure your network, understand what you are up against and deploy a policy, enterprise wide. Enforce secure physical security to your network at the word go; establish rigid rules and deploy a network security firewall; set-up a VPN( Virtual Private Network for your mobile employees and use https( hypertext Transfer Protocol Secure and SSH (Secure Shell) and enforce encryption throughout; install proper authentication systems, deploy monitoring of traffic and have systematized auditing processes in place.
- Secure the Wireless Network, Remote network and Roving users: The first thing to do when considering wireless networks is the physical security itself -- the Access points must be within the building and must be tamper-proof (reset buttons can revert the configuration to default values); default SSID must be changed and the “broadcast SSID” option must be disabled; change the cryptography settings, etc. Secondly, firewalls and all other software used for enabling this network must be updated regularly.
Best practices for Wireless Networking like enabling authentication and IDS (Intrusion Detection Systems) and implementing the WEP Standard, with 128 bit encryption should provide robust security to your wireless network and enable employees to work unhindered by wires and desktops.
- Secure the PC/servers and other Hardware: Adequate client-side virus protection software -- the best you could find which is constantly updated; Firewalls installed with appropriate configurations; Installation of a robust Intrusion Detection Systems (IDS); Updating the Windows Security Patches; and finally, a rigid application filtering policy to help filter streaming audio/video, pornographic content, Chat software, P2P software, and games and other non-relevant data for enterprises.
- Secure your email: Start with a granular, flexible, clear and realistic email security policy; solid Anti-spam, Anti-malware and Anti-spyware software are a must; ensure that you know what you are defending against and if you are doing it effectively or not make sure that all inbound, outbound traffic is monitored, including all web mail.
- Have a Disaster Recovery Plan: Cisco provides a wonderful approach leading to a flawless Disaster Recovery Plan. Firstly, senior management must take the plunge and formulate a security policy in the company; follow some best practices and these actions should be replicated and systematized across all levels in the company (creates ownership and induces responsibility).
The final plan would vary with the company in question but common patterns do emerge: your plan should take some critical factors into account such as the ease of implementing the security plan and the resources it would take; ease of deploying, installing and running the network security protocol; the flexibility of the scope of the network security solution in being able to allow you to run it satisfactorily, but still prevent it from outsiders.
 |
|
 |
Cisco SR 520 Remote Router: Designed for remote offices this router allows teleworkers to securely access all company internal applications and make calls from the outside |
 |
Cisco 5500 Series Adaptive Security Appliance (ASA): The ASA series offer advanced firewall features, IPS, Content security, and VPNs. |
Call (512) 356-9033 to talk to a CCIE Consultant
Or
Request a Consultant to call you:
Physical Security: Converge, Connect and Protect